Acronis Cyber Protect
Complete cyberthreat defense in one solution
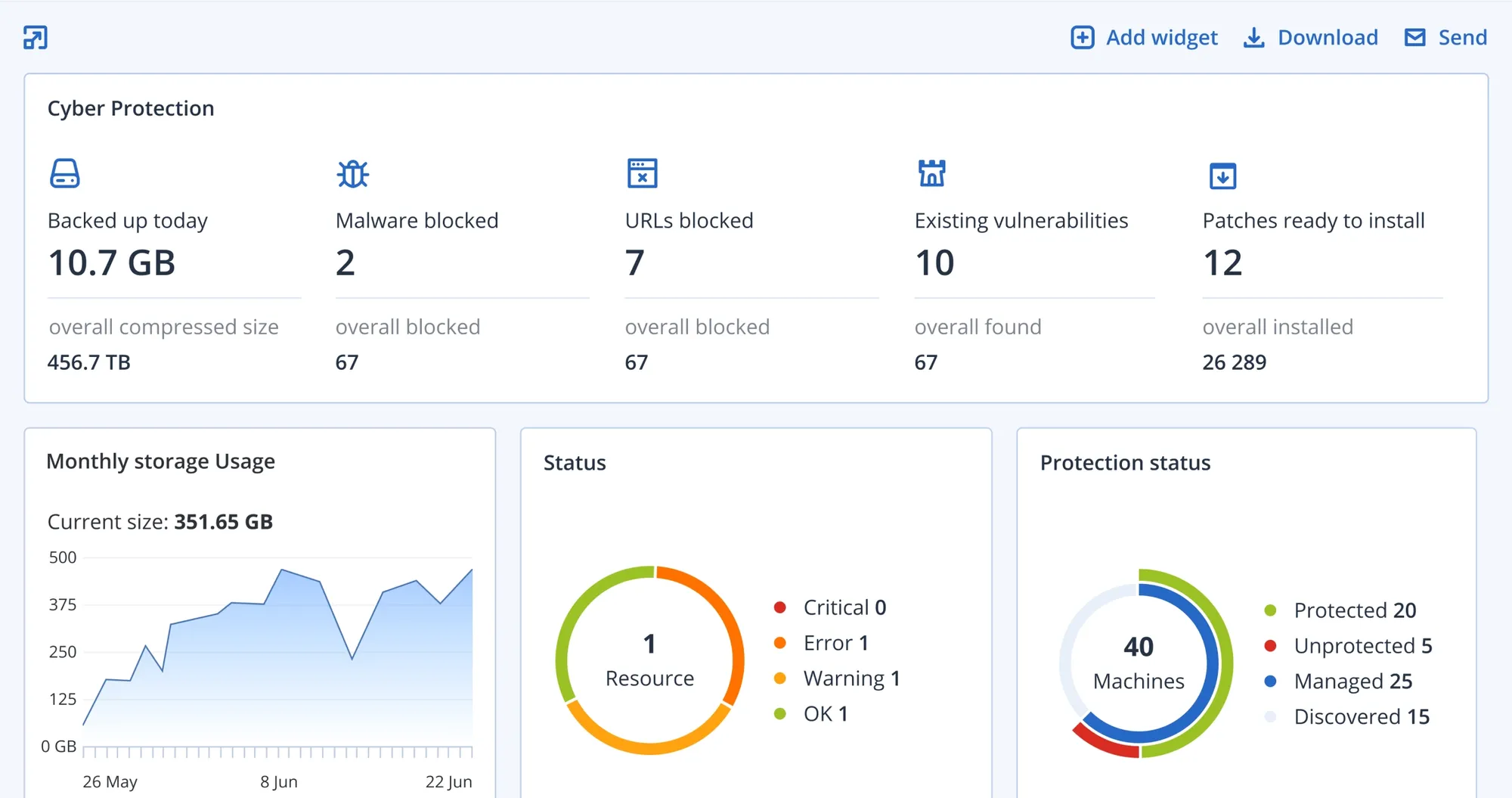
Acronis Cyber Protect seamlessly integrates the most secure backup with cybersecurity to provide complete, streamlined cyber resilience.
Overview:
Complete protection from security threats
Acronis Cyber Protect addresses these challenges by integrating backup and recovery with cybersecurity. This revolutionary approach eliminates fundamental complexity challenges, delivers better protection against today’s advanced threats, and maximizes resource efficiency
Extending Acronis Cyber Protect capabilities with comprehensive endpoint detection and response (EDR) enables customers to combat existing, emerging and new cyberattacks with a unique integration of protection technologies designed to prevent attacks, ensure business continuity and simplify security operations. Now, all cyber protection capabilities can be managed from a single pane of glass.
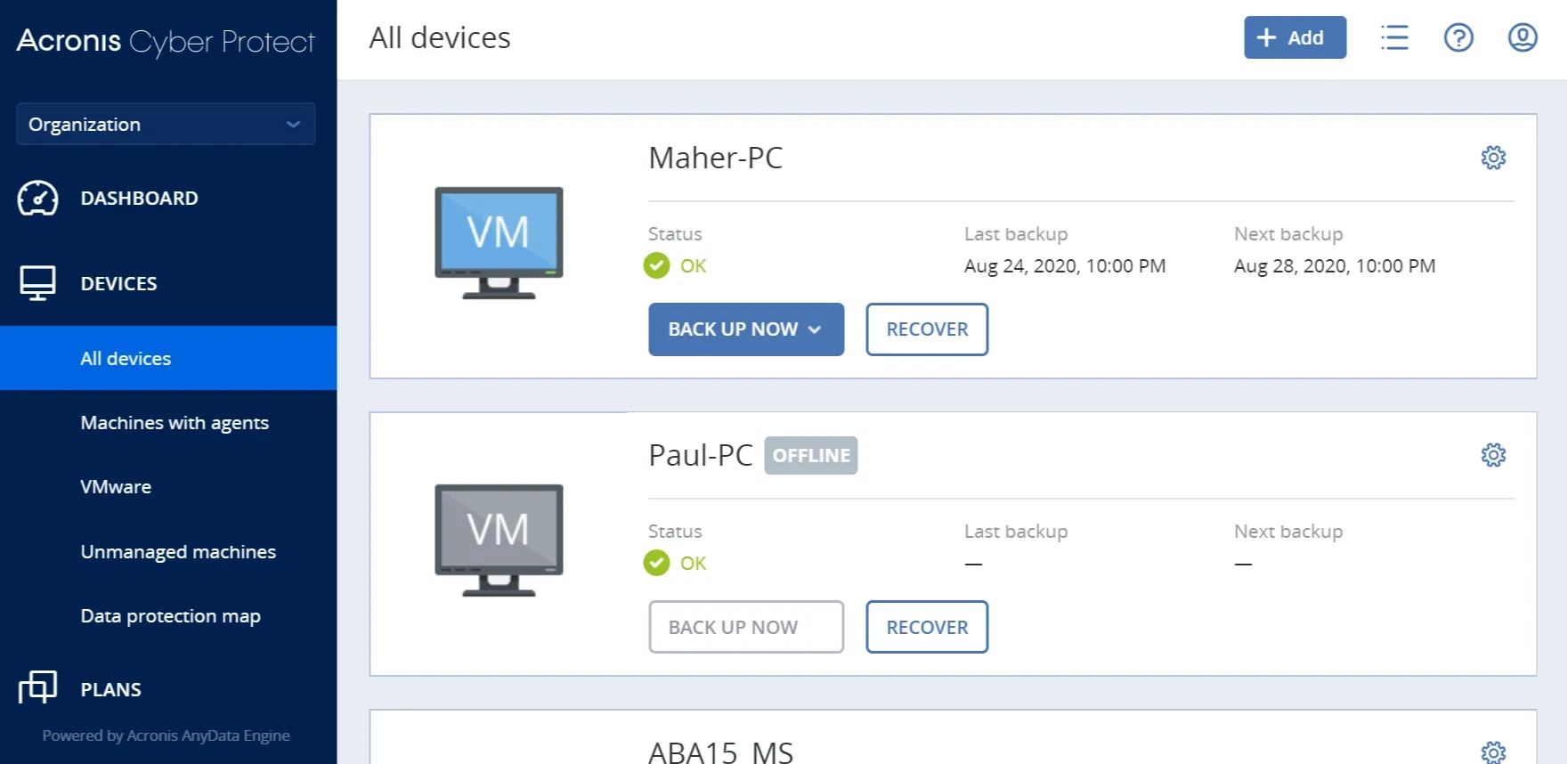
Easy, efficient and secure backup with rapid recovery
Simple Administration
- Consolidate security and data protection
- Eliminate performance or compatibility concerns
- Swiftly pinpoint and remediate any protection issues
- Automate routine tasks
- Effortlessly scale protection
Enhanced Efficiency
- Boost productivity by automating backup, security and endpoint management tasks
- Centrally manage all cybersecurity and backup, simplifying administration
- Reduce costs by consolidating backup, DR and security vendors
Advanced Security
- Detect and stop threats before they cause downtime
- Utilize informed response and investigation
- Deploy comprehensive security to ensure peace of mind
- Defeat ransomware with immutability and backup scanning
Centrally manage cybersecurity and backup
Advanced cyber protection for every endpoint in any location – making it ideal for today’s mobile and remote work environments.
![]()
Business continuity with cloud disaster recovery
![]()
Cloud-to-cloud backup of Microsoft 365, including free cloud storage
![]()
Proactive security augmented with endpoint detection and response

Three layers of cyber resilience
Advanced attacks can only be countered with advanced security
![]()
Proactive
Vulnerability assessments, patch management, security posture monitoring, threat hunting, and removal of malware from backups
![]()
Active
Continuous data protection, real-time threat protection, and informed threat investigations
![]()
Reactive
Rapid response to security incidents and recovery of data with attack rollbacks, integrated disaster recovery, and additional investigation capabilities like forensic backups and remote connections
See Acronis Cyber Protect in action
Explore how integrated cyber protection reduces complexity , delivers better protection against today’s cyberthreats and maximizes efficiency by saving you time and money.
Complete protection for modern-day threats
![]()
Endpoint Detection & Response
Advanced and unknown threat detection together with informed threat investigation and response.
![]()
Anti-malware and antivirus
Proactively protect your data, applications and systems from advanced cyberattacks with real-time protection, AI-enhanced behavioral heuristic antivirus, anti-malware, anti-ransomware and anti- cryptojacking technologies.
![]()
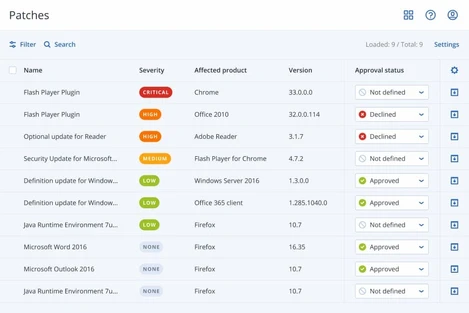
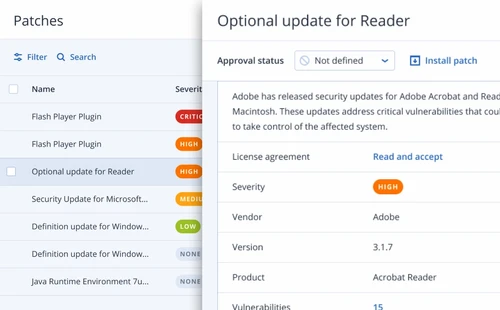
Fail-safe patching
Cyber Protect automatically creates a backup before any patches are applied to ensure that its quick and easy to recover if any installed patches cause system instability.
![]()
Forensic backup
Simplify future analysis, compliance reporting and investigations by collecting digital evidence – like memory dumps and process information – from disk-level backups with Forensic Mode.
![]()
Defeat ransomware
Prevent reinfection via integrated anti-malware scanning and malware removal during the recovery process. Gain peace of mind with immutable backup storage.
![]()
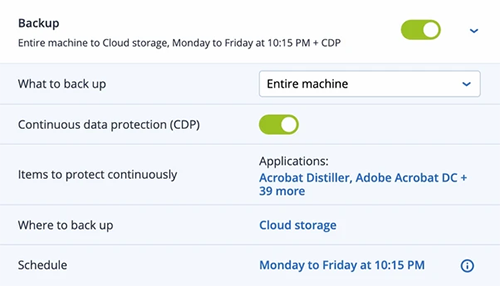
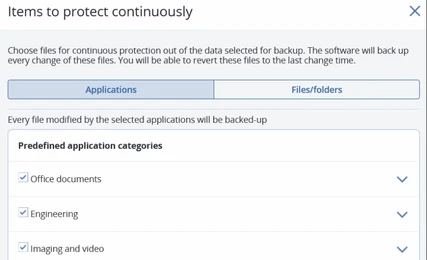
Continuous data protection
Safeguard new data as it’s created. Acronis’ agent monitors every change made in the listed applications and continuously backs them up so recent changes aren’t lost if the machine needs to be reimaged.
![]()
Global threat monitoring and smart alerts
Simplify future analysis, compliance reporting and investigations by collecting digital evidence – like memory dumps and process information – from disk-level backups with Forensic Mode.
![]()
Data compliance reporting and data protection map
Ensure compliance reporting by getting detailed information about stored data and use automatic data classification to track the protection status of important files.
- Pricing and product availability subject to change without notice.
- This product is available as instant electronic delivery upon purchase.
- Acronis Advantage Premier - Offers 24 x 7 support services available via phone, chat, and email. Acronis Advantage Premier customers receive priority support in the event of a business-critical system error (severity A), customers will receive the initial response within one hour. The first year of service is included with the Acronis line of corporate products.