
Acronis #CyberFit Score
Overview:
Acronis #CyberFit Score is the fastest, most cost-efficient way to assess the security posture of your endpoints, devices, and IT environment.
- Free tool
- No-installation required
- Detailed remediation report
- Based on NIST Framework
Use remediation reports to become more #CyberFit
Get expert advice from Acronis in seconds that’s based on industry best practices such as the NIST Cybersecurity Framework. Receive web-based remediation reports with recommendations for improving the security posture of your machines, which can be shared with IT personnel and end-users.
Assess your #CyberFit Score to improve your security posture
- Download for free
Get the lightweight #CyberFit Score tool at no cost - Run without installation
Compare the security configurations of your endpoint and IT environment against the industry’s best standards - Get a remediation report in seconds
Mitigate security risks and keep endpoints safe from cyberattacks based on informed, actionable recommendations

What is Acronis #CyberFit Score?
Acronis #CyberFit Score assesses and scores a set of security metrics to identify gaps in your IT environment and endpoints, and then makes recommendations on how to improve the organization’s security posture.
This resource is available as a standalone tool or as part of the Acronis Cyber Protect Cloud – the integrated data protection and cybersecurity solution for service providers.
- 74% of companies are not ready for a cyberattack
Based on their approaches to strategy, oversight, resourcing, and technologies/processes, three-quarters of survey responders ranked below the cyber readiness threshold.
Get Acronis #CyberFit Score along with Acronis Cyber Protect Cloud
Service providers can deliver superior business resilience through an integrated approach that eliminates any gaps in IT environments via a single solution:
- AI-powered
- Backup and disaster recovery
- Full-stack anti-malware protection
- Comprehensive endpoint management tools
- In-built vulnerability assessments and Acronis #CyberFit Score
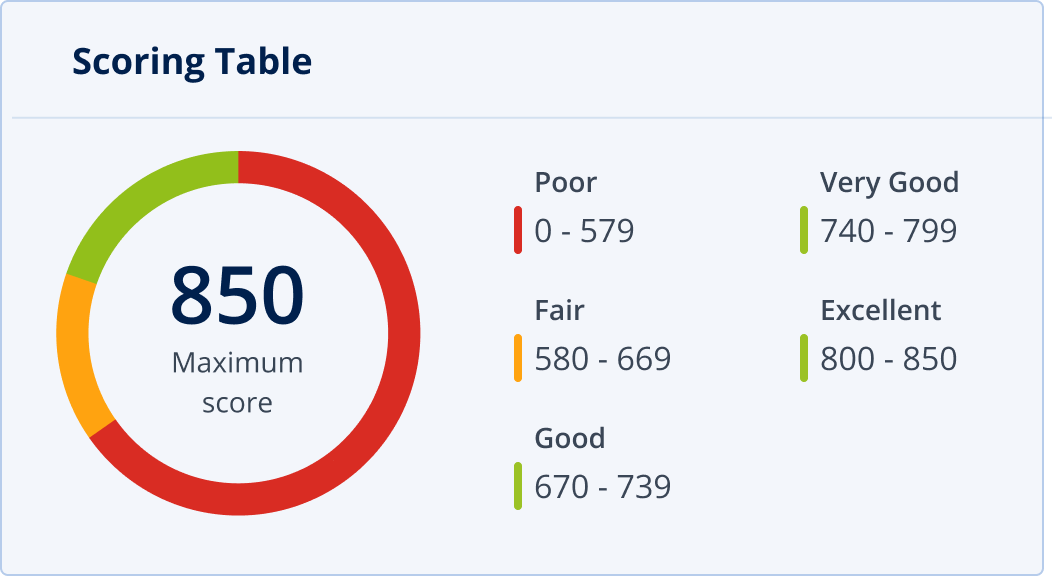
How is a #CyberFit Score calculated?
Acronis #CyberFit Score assesses multiple metrics – anti-malware, backup, firewall, VPN, disk encryption, and NTLM traffic. A score for each metric is awarded based how important they are to protecting a machine against cyberattacks. The scores of all metrics are then combined to form the Overall #CyberFit Score.
The scoring framework is similar to industry standards for security and risk-scoring solutions and U.S. credit ratings – making it simple to show each metric so it’s easily understood by users.
- Pricing and product availability subject to change without notice.
- This product is available as instant electronic delivery upon purchase.
- Acronis Advantage Premier - Offers 24 x 7 support services available via phone, chat, and email. Acronis Advantage Premier customers receive priority support in the event of a business-critical system error (severity A), customers will receive the initial response within one hour. The first year of service is included with the Acronis line of corporate products.
