Acronis Detection and Response
Add a layer of security to detect, stop, and analyze threats that evade other defenses

Threat-Agnostic Security
Add threat detection and response to supercharge your endpoint security. Prevent attacks that evade anti-malware defenses, including new or unknown malware
Real-Time Threat Prevention
Stop being reactive to security breaches by deploying a proven solution that automatically prevents the damage from occurring.
Focused and Detailed Visility
Empower your security team with granular visibility into attack timelines, origin, tactics, techniques, and procedures.
Overview:
Prevent Attacks in Real-Time and Gain Deep Visibility Into Every CyberThreat
Acronis Detection and Response is a last line of defense that protects your organization against threats that evade your anti-malware defenses. Designed around the zero trust approach, the solution detects and prevents any deviations from legitimate OS behavior and provides real-time visibility, as well as automatic and manual remediation capabilities.
![]()
Threat-agnostic security
Add threat detection and response to supercharge your endpoint security. Prevent attacks that evade anti-malware defenses, including new or unknown malware and ransomware, fileless attacks, zero-days, and advanced persistent threats (APTs).
![]()
Real-time threat prevention
Stop being reactive to security breaches by deploying a proven solution that automatically prevents the damage from occurring. No manual threat hunting, costly infrastructure, or cloud connectivity is required.
![]()
Focused and detailed visibility
Empower your security team with granular visibility into the attack timelines, origin, tactics, techniques, and procedures (TTPs), as well as information on what the attackers attempted to accomplish, to strengthen your organization’s security posture.
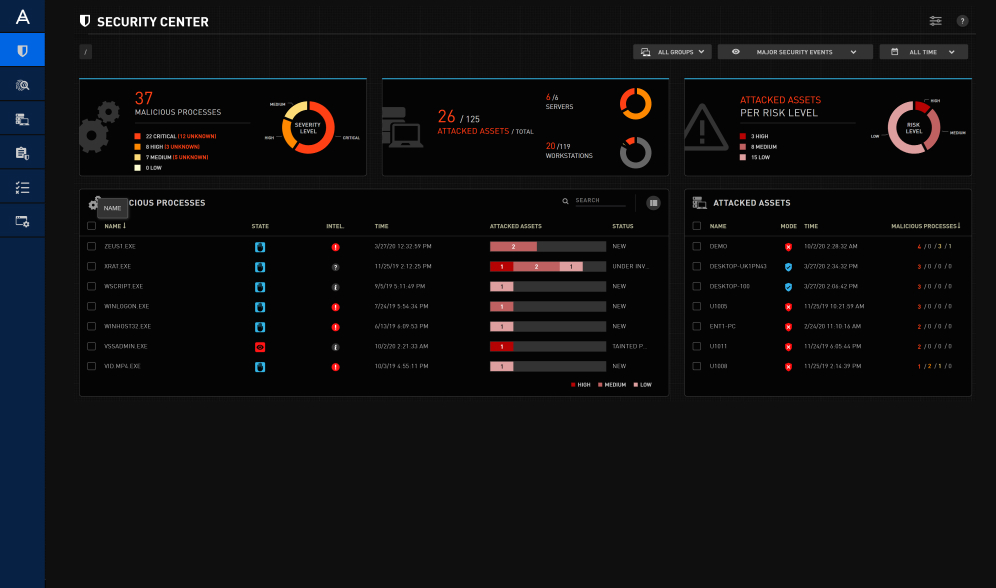
Minimize incidents and improve productivity
Prevent more attacks and minimize risks
Enhance your organization’s security posture and stop breaches before they are able to do harm. Detect and prevent the advanced attacks that bypass your anti-malware defenses, including new or unknown malware and ransomware, fileless attacks, zero-day threats, and APTs. Benefit from a zero trust approach for better detection accuracy and catch any deviation from legitimate OS or application behavior, even in offline or air-gapped environments.
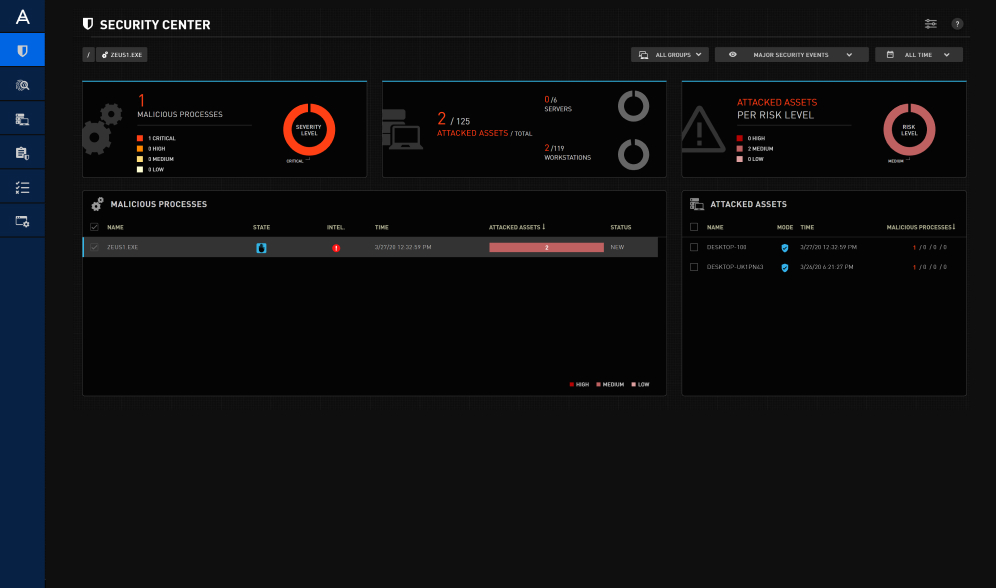
Ensure rapid incident response with deep visibility
Continuously monitoring endpoint and network activity across the entire organization to ensure focused, detailed visibility into any threat. Reduce response times with automatic threat prevention capabilities. Empower your security team to provide manual remediation and post-breach investigation with detailed visibility and forensics into every attack.
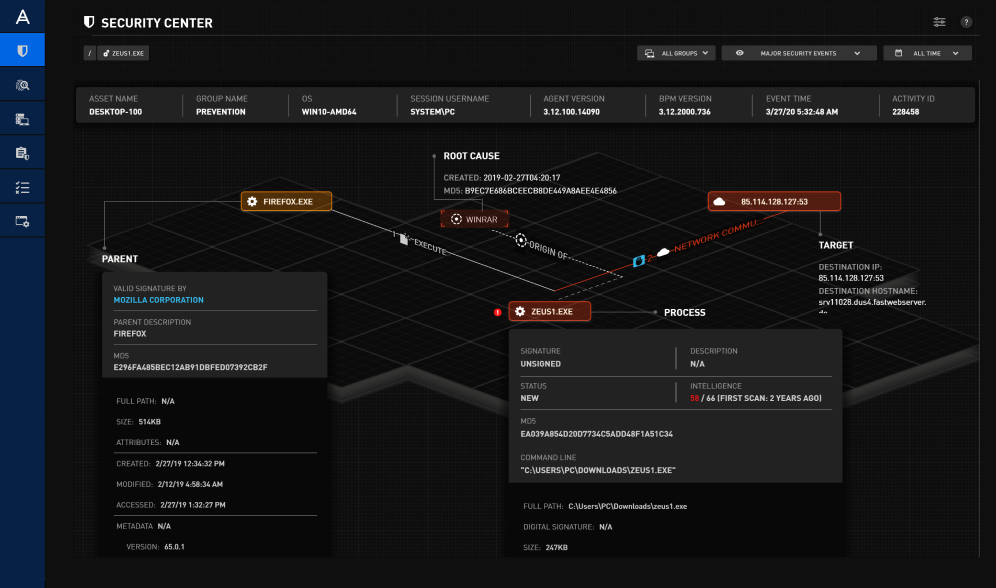
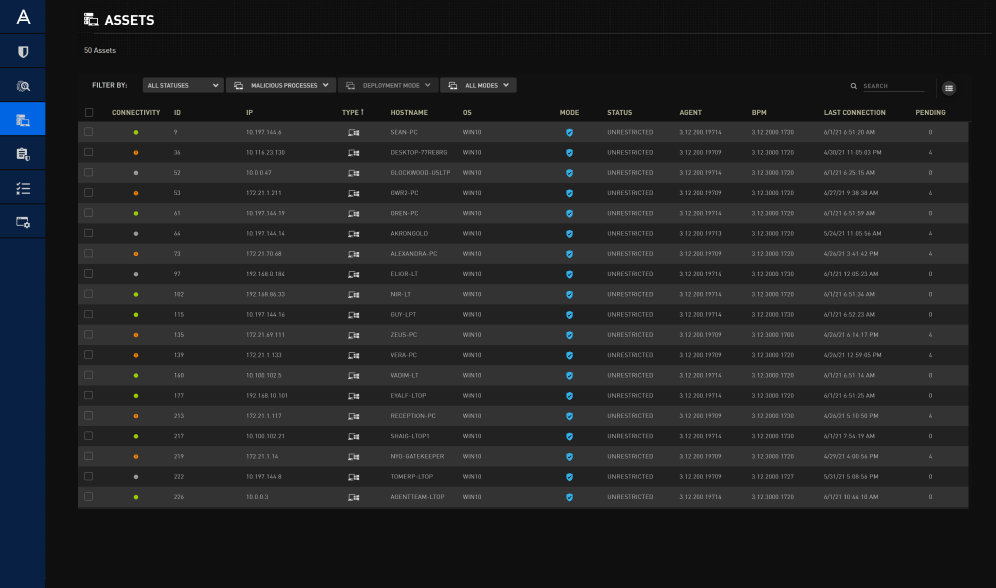
Leverage your existing resources to the fullest
Implement a last line of defense for advanced threat detection and prevention that supplements your existing anti-malware defenses, such as Acronis Cyber Protect – no need for a rip and replace solution. Reduce staffing needs thanks to automated threat hunting with focused, detailed visibility into threats without unnecessary noise. Lower your total cost of ownership (TCO) even further via low bandwidth consumption, eliminating the need for costly infrastructure.
Benefit from a modern approach to threat prevention
Acronis Detection and Response adds post-breach threat detection and response capabilities to your security stack. Identify and stop threats that have bypassed other defense layers while empowering your security team with deep, forensic analysis on each incident.
Automatic, real-time protection
Automatically stop threats once detected, unlike solutions that require manual or semi-manual threat hunting and remediation.
Threat-agnostic protection
Block sophisticated threats that evade conventional defenses such as APTs and zero-day attacks with a unique CPU-level analysis that allows action earlier in the attack chain than other technologies.
No data deluge
Empower your service delivery and security teams with direct access to cyber analysts and email security experts that monitor all customer traffic and analyze malicious intents with ongoing reporting and support.
Low TCO
Leverage an unmatched detection speed that allows you to prevent all threats before they reach end-users, compared to the reactive approach of standard email security technologies.
Zero trust approach
Increase the threat detection accuracy with a zero trust approach, identifying any deviations from legitimate OS or application behavior instead of having to identify constantly evolving attack techniques.
- Pricing and product availability subject to change without notice.
- This product is available as instant electronic delivery upon purchase.
- Acronis Advantage Premier - Offers 24 x 7 support services available via phone, chat, and email. Acronis Advantage Premier customers receive priority support in the event of a business-critical system error (severity A), customers will receive the initial response within one hour. The first year of service is included with the Acronis line of corporate products.