The Latest Acronis News
Product and Solution Information, Press Releases, Announcements
Acronis Earns Second Place in AMTSO Cryptojackers Detection Test, Beating Many Leading Endpoint Cybersecurity Solutions
August 30, 2019 By BlueAlly

In addition to ransomware, cryptojacking – or illicit cryptomining – continues to be a major headache for companies and home users. In fact, recent research from SonicWall found that cybercriminals made an impressive $52.7 million by mining digital coins on victims’ machines during the first half of 2019.
Acronis experts also see a clear connection between cryptojacking criminal activity and the prices of major cryptocurrencies. Unfortunately, the overall trend of attacks is growing.
NioGuard Security Lab, a member of Anti-Malware Testing Standard Organization (AMTSO), researched the matter and just posted a report that examines the level of protection against cryptojacking offered by leading endpoint security providers.
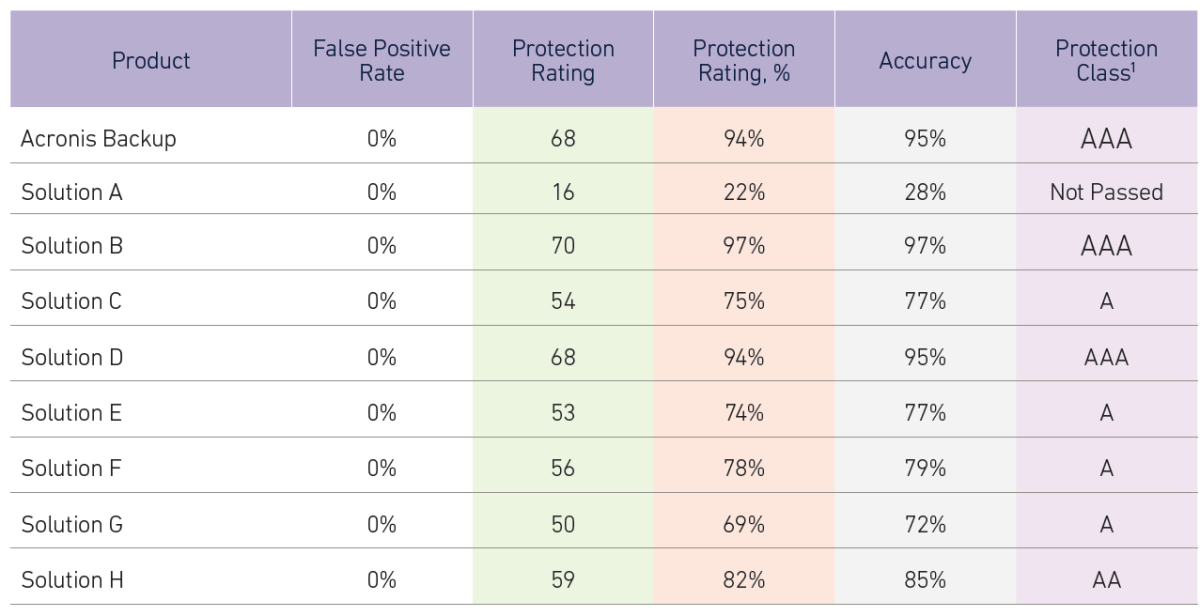
The results might shock some observers because Acronis, which now defends against illicit mining in its data protection solutions, outperformed the vast majority of these leading endpoint security providers. It was one of only three solutions to earn a Triple-A rating and tied with another vendor for second place.
Following AMTSO’s independent standards
The study followed AMTSO’s standard procedure for fair, transparent, independent testing. Acronis commissioned the test to measure the performance of its anti-cryptojacking defense, which is built into its data protection solutions – both Acronis Backup for businesses and Acronis True Image in the consumer space.
The Test Report indicates how effectively each of the products detected the threats in real-time. It is important that the study followed the AMTSO Testing Protocol Standard and is subject to a compliance check by AMTSO. (For more information see the test page.)
Unfortunately, while the highest level of transparency is desired, NioGuard reports that several endpoint security vendors opted out of the study – often before seeing the results. As a result, the names of other solutions are hidden and simply assigned generic titles of “Solution A,” “Solution B,” etc.
Comprehensive set of test scenarios
The test included the following scenarios:
- Publicly available cryptominers.
- Packed and/or obfuscated versions of the cryptominers mentioned in item 1, in order to exclude signature-based detection.
- Malware that starts cryptominers on an infected host.
- Negative tests that included legitimate everyday activities that result in high CPU/GPU loads.
All told, there were 22 versions of various cryptominers included in the test, some of which use CPU power while others rely on the GPU to generate crypto coins.
Measures, ratings and results
The test measured True Positive Rates (TPR), True Negative Rates (TNR), Accuracy of Detection, and Protection Rating. To assign a Protection Class (AAA, AA, A), the tested products were organized with the help of Hierarchical Clustering, taking into account their Protection Rating. A higher Protection Class was assigned to the products within the cluster that had a higher average Protection Rating. If a product earned less than a 50% Protection Rating, it did not pass the test and was excluded from the Protection Class assigning procedure.
In reporting its findings, NioGuard reported that “As a result of the test, Acronis Backup 12.5 earned the highest protection class AAA, showing very good protection capabilities to detect CPU and GPU cryptominers, with a Protection Rating equal to 94%”.
Final thought
Given our commitment to protecting all data, applications, and systems, combatting a growing threat like cryptojacking is a critical consideration. Not only does the additional workload on your computer caused by this kind of malware slow your computer’s performance and increase energy costs – an infection can expose your system to other risks since cryptojackers are frequently bundled with ransomware.
At Acronis, we were excited to see such excellent results; especially since Acronis Active Protection, the defense we integrate into our data protection solutions, out-performed the products that dedicated endpoint security vendors offer.
Of course, we know that cyberthreats are constantly evolving, so we remain dedicated to constantly improving Acronis Active Protection. That way our technology continues to deliver better protection from malware such as ransomware cryptojackers.
